Research - (2023) Volume 11, Issue 1
A Blockchain Applications and Challenges
Amal Abdulbaqi Maryoosh1*, Ahmed Abd Ali Abdulkadhim1 and Muntaha Abdulzahra Hatem22Mission and Cultural Relations, Ministry of Higher Education and Scientific Research, Iraq
Received: Jan 04, 2023, Manuscript No. IJCSMA-23-85478; Editor assigned: Jan 06, 2023, Pre QC No. IJCSMA-23-85478 (PQ); Reviewed: Jan 16, 2023, QC No. IJCSMA-23-85478 (Q); Revised: Jan 21, 2023, Manuscript No. IJCSMA-23-85478 (R); Published: Jan 28, 2023, DOI: 10.5281/zenodo.7824443
Abstract
Block chain is a technology for securely storing data in a manner that makes system changes or hacks impossible or difficult. Numerous organizations have adopted this technology, which utilizes a peer-to-peer distributed network. Using a decentralized peer-to-peer network to operate. A block chain is a collection of linked computer systems that operate as a distributed ledger of transactions. Every new transaction that happens on the block chain is copied to each participant's ledger, and each block on the chain is made up of numerous transactions. This paper aims to explain block chain technology, including its uses and difficulties.
arion-krmiva kupispredas rottoconsultants hattrennet insurancemarketingpros abcoelectricli paddriver bobcoironrailings cliniquemtarhemodialyse gtech settechny groupe-saturne caffeitaliany rcollision husoghytteplan okba-medicaments mazex atyourserviceoil hetgroenewerk msgfeather rolltech ismllw lorlin conceriacaponigiuseppe chouikha-big dona-hotel ibrax fullthrottleeventplanning theblindspotli mustakynnys curdent auprintemps koulouritispolis floorbufferbrush minicoindustries thespongecompany localvisits fixcars baofoto poi elvisnewman palestragymtonic cavalierifuel unityrubberproductsllc menuiseriemorlighem nugris skillslab mecanica vksim brcanvas handfordoil lemi-yhdistys schoolbuspartsnow thebestofchampaign testingmechanics comm-unique goodnewsbooks generaldecor campye defence-institute fairwaymanorllc whpdc regionalsigns babuin islandeastdentalgroup sirajeslov adda thebestofcleveland integraff sealfiberglass nutechsys tcilandscaping digitaltechsquad tomsvetteshop funda-mantels rahaanopeasti thebowmanfirm marshallcoffeeny mrbrushes sicop-pentacol myguyappliance ldclean ephesusmedcuisine alphafastenersusa unitysurfacing allseasons-mechanical easyketodietsuccess liusaari strongarmcleaningny josg sterlingcutter unadesinfection huizebuitenhuis thebestofraleigh drcentralbaking catsol traditionaltrainsandhobbies goelectricnj casaconcreteinc thebestroofingcompanies autoproautomotiveservice general-machine djsensationalsounds fevaagbaatforening straightlinecustomconstruction impianti-antizanzare thebestoffortworth rosanneebner edandson americanchoirgown violiner jeromeandleighcrutch promisinguk iasautomotive scrittori plasticsrecycling giuseppedainelli jerryspride prontointerventoelettricista24h fimad gdezinewraps kimmokakko tracony fiavet bwnivelles alsalamzorg septimus pdcfundraising hoteldellaspina francobianchi cleansweepcremations errachid thebestofeugene grossoregistratori brotherspastries bellmoreglassandmirror plasmapreen microdecisionsystems eternoholdings alessiocostruzioni hotelpisa excelcourtreporters gmstow tatsrl chateaulamercatering bargaouirideau shcarwash shipritebags allportstrucking juventuspizza red-agri licorneargent thebestofphiladelphia lewisy greenrecuperi thebestofindianapolis fosenlagetsangkor coastweldingsupply nyfixcars alshubcaps hanssenspronkfamilierecht scottsafe barbatonursery jelconst jerryshulmanproduce orchardrealty minervasbandb dialindustries phytosif icredit thebestoftallahassee malermester-blakstad morvayautosiskola tektronicsinc cance-tu-asbl bicotec martinsqualitytruckbody paprikalongbridge roger-jensen rockypointbarbershop rmkdistributors tommiriiulid atlaschemicalllc gopaverinstaller onyxchb thewindowmill khalfallah-pneus ciaociao lexilogistics tipografiaelleemme thebestofwichita cdvdpro roll-n-roaster repelrestoration kcfapi ivar-moe bacosport byggkonsult predicate rohanengineeringpc footpharmacydirect solidbox piovesan visserijverduurzaamt toscanibus sixgsroofing tecnocostruzionizella outsourcemarketingpros pilotexamsdgca carraihome royalbakersdist guardiedicitta bestbaby-tn littlechicken werks1inc hodsonoilco surfacingsystems lckcabinetry pbtools4u set-mfg serristoricountry goldenmoonusa fourcmanagement lioutdoorliving nova-euro-fashion lavecchiacascina pomaraf novamaille dkstechnoholdings liisasauso sahel-tunisie inspired-tech aldamartini monarchengraving craldipendentiuslprato centuryhardware scholengroep ourtowncarwashandquicklube mayablog geometraparisi ash-grove tendertoo smithoilcompany westfrieslanddakbedekkingen lamaisonbeb blog ebiketime laurenty puurklant vincentwielders chams nassausuffolkirrigation bbdps aerocbt fursbysuperior unityrubbercompany horizonconceptinc immstema vhujon nativelandsmokeshop kaabia-orthodontie locali brooklynterminalmarketonline transportopplaering neonmazesl kuturanta apsbox federalnetworks liontrading power-tran degryse-chauffage uniquemasonrycorp proramps catchasilverstar projectbinder unityllc italyvacationpackages rrappliances norwestac topspintennisli boatfindertransport sblcollege imperialvendinginc nanea igiardinidibeatrice pslniemela holycowindian sisekosmosejaam acquadirete obertaberhof thebestofdallas betterheader mrpickleinc medspareparts thebestofsacramento toyotavandergeest alliance-consulting scbox sshoreendo thebestofgreenbay fiducia-partner komunikujeme lapetitemaisonenfrance chesterplastic wisesystems terveysverkko oportal cjflagandson gold-estate spiriolaw salvatorechiarelli autoskola trendcreditcorp scooterkingalmere sisternibedita thebestofminneapolis cerealism transnationalusa homedelano francobenvenutiartista kulsaasvelforening florencevillavioletta gettingerfeathers touchofclasscoll tomkovci
Keywords
Block chain, Bitcoin; Cryptography; Network; Internet of Things
Introduction
To construct Bitcoin, block chain technology was developed. Presented to the world in 2008 in a white paper entitled "Bitcoin: A Peer-to-Peer Electronic Cash System", written by an author who has never been identified by their real name, Satoshi Nakamoto. Bitcoin's declared purpose was to lower transaction fees, fraud, and payment uncertainty in online transactions. It was put forth as a substitute for the widely used e-commerce model, which depends on financial institutions acting as trusted third parties to process electronic payments [1].
A block chain is a series of blocks that functions as a public ledger for all committed transactions. This chain grows when additional blocks are added to it. Decentralization, persistence, anonymity, and audibility are important characteristics of block chain technology. Block chain can function in a decentralized setting by fusing important technologies like cryptographic hash, digital signature (based on asymmetric cryptography), and distributed consensus process. Using blockchain technology, a transaction can be carried out independently. Blockchain can significantly reduce expenses and increase efficiency as a result [2].
As opposed to a conventional database, which is controlled by a single entity like banks or governments, A Block chain is not someone's property. With a vast network watching over it, it becomes nearly hard to tamper with the system by fabricating documents, transactions, and other information. Block chain is a network of nodes that stores data forever. By doing this, the information is distributed as well as decentralized (Figure 1). A localized version of the Block chain technology that is updated on a regular basis to maintain consistency across all nodes, can be stored locally by each node in the network. A block chain is a platform for decentralized computing and information exchange that enables numerous nodes, which do not trust one another, to participate in decision-making. The single point of failure in a centralized system is the issue. A decentralized system avoids having a single point of failure by having numerous coordinate points. Each node works together to complete the task in a distributed setting. A node connected in a distributed manner is used to represent each user. A replica of the regularly updated Block chain list is kept on file by each node. A node can carry out a variety of tasks, including mining, transaction validation, and transaction initiation [3].
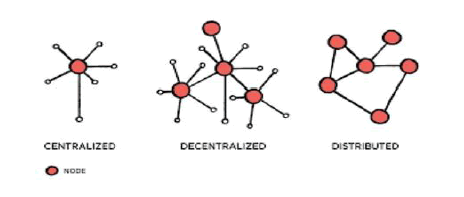
Figure 1:Block chain as distributed Technology.
In this paper, we will spotlight about the applications of the block chain technology and the challenges which faces this technology. The remaining sections in this paper are as follow:
Section two explains how the block chain works. In section three we show the types of block chain networks. Section four displays the applications of block chain technology. In section five we explain the most important challenges that facing block chain technology [4].
2. How does block chain work?
A node in a network notifies all other nodes of a transaction whenever it gives money to or receives money from another node. In essence, the information indicates that payment of value X was made from node A to node B at a particular moment. A third node, known as a miner, checks the legitimacy of the transaction before registering it in the distributed ledger. A large number of transactions are registered at once in blocks. A new block must be connected to the earlier blocks in some way because these blocks of transactions can be produced by many nodes in the network. Each new block in a block chain is "chained" to the older blocks by means of a cryptographic signature. While very difficult to duplicate, this signature is simple to validate. It is produced by the cryptographic process known as hashing, which uses a significant amount of information as input to produce a special identification known as the "hash value" or "digital fingerprint." It is difficult to reconstruct the data that produced the hash value via hashing. Miners are nodes that create new block [1, 5]
In the Bitcoin network, a consensus method known as proof of work (POW) is employed. For authentication, POW needs a challenging computing procedure. In POW, each node in the network computes a hash value of the block header, which is continually updating. According to the consensus, the estimated value must be less than or equal to a specific given value. To reach the aim in the decentralized network, all members must continuously calculate the hash value using various nonce. All other nodes must mutually verify the accuracy of the value when one node obtains the pertinent value. Then, in the event of fraud, the transactions in the new block would be verified. Then, a new block is added to the block chain to represent the authenticated result, which was determined from the collection of transactions utilized for the calculations. The POW mechanism is known as mining, and the nodes that calculate the hashes are known as miners. An incentive mechanism (such as giving the miner a small share of Bitcoins) is also suggested because calculating the authentication is a time-consuming procedure [2]. The Sybil or 51 per cent assault, which happens when a malicious actor controls a majority of the nodes and then decides to reach a consensus against the interests of other network users, is one of the risks to the block chain. [1].
3. Types of Block Chain Networks
A Block chain depending on its applications can be classified into public, private, or hybrid [6, 7] as shown in Figure 2
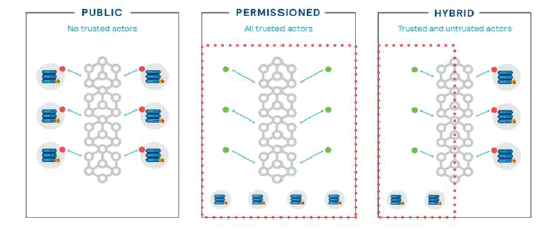
Figure 2:Types of Block Chain Networks.
3.1. Public Block Chain
Public block chain is a fully decentralized network, it has no single owner, is permission less, visible by anyone, and with no individual or entity controlling it. All transactions are fully decentralized and transparent by allowing anyone to participate. Bitcoin is an example of a public block chain.
3.2. Private Block Chain
A private block chain (also called permissioned) is distinguished from a public block chain in that it is centralized participants are required to ask for consent to join the network. Only the entity inside the network will gain permission to write to and read from the block chain. Because a single entity owns and controls the creation of blocks, consensus procedures and mining are typically not necessary.
3.3. Hybrid Block Chain
The hybrid block chain, also known as consortiums, has some features of the private block chain, such as scalability, security, and privacy protection level. The main difference is that type nodes, such as the leader node, are selected to verify transactions instead of a single entity. Only authorized members are given copies of the block chain, making the network partially decentralized [8].
4. Applications of Block Chain
The applications of the block chain have expanded to include many areas while it was in its infancy an application for crypto currencies. As its uses have expanded to include many areas such as supply chain management, internet of things, energy-saving, advertising verification, healthcare, and etc. With the creation of user friendly interfaces and new use cases, it is anticipated that we will see applications that are more beneficial in the future. Businesses and sectors are motivated to explore and build Block chain based applications for a variety of reasons, including access to information, data integrity, and operational resilience [9].
4.1. Financial Applications
One of the biggest challenges of the financial industry is the centralization of financial institutions. This contradicts the special feature of Block chain technology. However, recent development in the type of technology has addressed this problem. Another challenge is the transaction per second of the financial institution. Aside from that, cost initiation, implementation, and maintenance are of major concern. These require a great amount of funding to initialize and implement because the whole system includes the hardware and software. Moreover, financial institutions require large-scale integration and migration from the previous system and maintenance of the whole system. Implementing this might be a big issue for a small financial institution. It also requires expert personnel to implement, maintain and operate the system, since Block chain is still under development as a whole, technical training is not yet in-depth across the network and its application [7].
4.2. Internet of Things
The using of Block chain technology with Internet of Things (IoT) can enhance security and privacy. Block chain eliminates the idea of centralized IoT and allows for the secure and efficient transfer of data for every transaction. With the aid of block chain-IoT integration, a number of important applications for smart environments were created. These apps' prototypes must be studied in order to identify and address their flaws. Here, we list few Block chain technology applications for IoT [7, 9, 10]:
• Energy trading.
• Internet of vehicles.
• Internet of Healthcare things.
• The cloud as a potential platform.
• Implementations in a smart city network.
• Applications in Industrial Internet of Things.
4.3. Healthcare Applications
When using Block chain technology in Electronic Medical Records (EMRs), EMRs are current and offer secure, private sharing of patient data among numerous providers. Block chain technology in healthcare has benefits beyond security and privacy. Regardless of their electronic medical systems, doctors, hospitals, patients, and all other stakeholders might access a shared database of health data and information on the block chain. Its use frees up more time for doctors to care for patients and share more research findings that could lead to the development of new therapies. By making results more available and reducing claim and billing fraud, it helps improve medication development. Block chain is transforming how the healthcare sector runs [7, 9].
4.4. Smart Contracts
When implemented on the block chain, a smart contract is a computer system or collection of code and data that executes automatically based on predetermined criteria [11]. Without the use of middlemen, smart contracts offer the chance to exchange money, shares, properties, and other assets directly. Users of the Ethereum network can develop "smart contracts." Any machine with the Ethereum software installed can be used for this [12].
Smart contracts can be used to detect and stop malicious behaviour. The system rejects the device's breached block chain updates. In cases where devices don't require centralized devices for secure communication, they also get rid of centralized organizations. Instead, with the aid of smart contracts, they may safely connect with one another, share data, and carry out operations autonomously [13].
4.5. Education System
There are various issues that arise in this day and age when school instruction is delivered online. Classes are condensed, and the teacher must continuously check to see who is in the class, taking up valuable time. Each school's administrator is also interested in finding out if the staff teachers hold their classes consistently and on schedule. If the data from each class were stored on a block chain, these issues might be solved. No one will be able to modify the data that way. You can always find out who taught the class, when they taught it, and who showed up. Students would attend lessons more frequently if they were aware that everything was recorded and that the information was unchangeable. And it is an essential requirement if they want to increase their success. For instructors, the biggest satisfaction comes from increased student achievement. Parents would likewise be happier if their kids behaved in this way. A good education would be most advantageous to society as a whole because knowledge is power. And it is an essential requirement if they want to increase their success. For instructors, the biggest satisfaction comes from increased student achievement. Parents would likewise be happier if their kids behaved in this way. A good education would be most advantageous to society as a whole because knowledge is power [11].
5. Challenges of Block chain
The block chain has a lot of potential, but it also has a lot of problems that prevent it from being widely used. In this section, we will discuss the most important current challenges facing block chain technology.
5.1. Privacy
Block chain can preserve a certain amount of privacy and security of data processing, however, it is cannot guarantee transactional privacy because collected data are publicly visible and available for all readers. According to a recent study, it is possible to link a user's Bitcoin transactions and learn personal information about them. Furthermore, open ledgers could cause privacy problems because IoT ubiquitous sensing technologies continuously capture sensitive and personal data from customers [14, 15]. Data privacy could be secured with private block chain ledgers by enabling encryption and granting restricted access to the ledgers. However, these private block chain systems will restrict how much of the vast amounts of data that AI may need to digest and carry out accurate and correct decision-making and analytics may be accessed and exposed [15].
5.2. Scalability
One of the main issues with the block chain platform of today is its scalability. The block chain grows in size as more transactions are made every day. Since they must determine if the source of the current transaction is unspent or not, each node must store all transactions in order to validate them. Additionally, the Bitcoin block chain can only process about 7 transactions per second due to the original restriction on block size and the time interval used to generate a new block; this performance is really unacceptable when compared to Facebook, which processes millions of transactions every second, including likes, posts, and comments. Since the capacity of blocks is so low, many minor transactions may be delayed since miners prioritize those with significant fee income. Several initiatives have been put out to remedy the blockchain's scalability issue, such as storage optimization of blockchain and redesigning block chain [14, 15].
5.3. Security
Block chain technology's decentralized power is subject to exploitation and misuse. The block chain systems are susceptible to cyberattacks like that 51% attack, despite the fact that block chain offers strong methods for safeguarding IoT and predictive analyses. In public block chains like Ethereum and bitcoin, this security issue is more obvious. Because consensus methods are specified among parties, private block chain platforms are less affected by this issue. Additionally, the mining nodes' operating environment is not secure, particularly on private block chain platforms like Hyperledger with a small number of mining nodes, where the results of the execution might be changed. Newly emerging block chain technologies, such Intel SGX, are outfitted with hardware to provide execution in a Trusted Execution Environment to address this issue [15].
6. CONCLUSION
Block chain is a peer-to-peer, decentralized digital ledger that is accessible to the public. Numerous applications of block chain allow transactions to be carried out in a secure setting without the involvement of a third party. Block chain technology has the potential to transform the current centralized system into a decentralized one from the perspective of applications. The Internet of Things (IoT), healthcare, and other application areas have been listed as some of the most demanding. Block chain technology has many benefits, including decentralization, transparent transactions, openness, and security. However, more study needs to be done on the block chain system's network, scalability, and mining process.
References
- Nations, U. (2021). "Harnessing rapid technological change for inclusive and sustainable development." Unctad. [Google Scholar] [Cross Ref]
- Zheng, Zibin, et al. "Blockchain challenges and opportunities: A survey." Intern J Web Grid Ser. 14.4 (2018): 352-375.
- Mohanta, B. K., et al. "Blockchain technology: A survey on applications and security privacy challenges." Inter of Thin. 8 (2019): 100107.
- Ahmad, P. "A review on blockchain’s applications and implementations." Adv Distrib Comput Artif Intell J. 10.2 (2021).
- Crosby, Michael, et al. "Blockchain technology: Beyond bitcoin." Appl Innova. 2.6-10 (2016): 71.
- Sultan, K., et al. "Conceptualizing blockchains: Characteristics & applications." (2018).
- Villanueva, N. E. "Blockchain Technology Application: Challenges, Limitations and Issues." J Comput Innov Eng Appl. 5.2 (2021):8-12. [Google Scholar]
- Fuchs, P. (2019). "Blockchain." 1-22. [Google Scholar]
- Baiod, W., et al. "Blockchain technology and its applications across multiple domains: A survey." J Int Technol Inf Manag. 29.4 (2021): 78-119.
- Ebrahim, M., et al. "Blockchain as privacy and security solution for smart environments: A Survey." ArXiv. (2022).
- Mijoska, M. & Blagoj, R. "Possibilities for applying blockchain technology–a survey." Informatica. 45.3 (2021).
- Utakaeva, I. K. "Directions and features of application of the blockchain technology." J of Phys. 1353.1 (2019).
- Tariq, N., et al. "The security of big data in fog-enabled IoT applications including blockchain: A survey." Sensors. 19.8 (2019): 1788.
- Gayathri N. R. M. "Blockchain Technology Architecture And Key Characteristics." Ijariie. 4.4 (2018): 1264-1268. [Google Scholar]
- Salah, K., et al. "Blockchain for AI: Review and open research challenges." IEEE Access. 7 (2019): 10127-10149.